Both pfsense and astaro are running NAT, but aren't behind NAT. I tried playing with that setting in a few different ways. Anytime I change the VPN ID the tunnel dies until I set the peer address to that same IP on the pfsense. I used the Sophos UTM9 product for a few years but outgrew the 50 IP address limitation so moved to pfSense. I really liked UTM and was never really happy with pfSense as I always felt UTM had a much better interface and the FW rules were more logically configured. PfSense Plus for cloud Enterprise, Open Source SOLUTIONS Providing comprehensive network security solutions for the enterprise, large business and SOHO, Netgate solutions with pfSense Plus software bring together the most advanced technology available. As pfSense is based on FreeBSD, its hardware compatibility list is the same as FreeBSD's. The pfSense kernel includes all FreeBSD drivers. PfSense 2.5 (FreeBSD 12.2).
This article explains how to configure IPSec VPN Site to Site between Sophos XG firewall and Pfsense firewall devices
This aritcle configured according to the following diagram:
Photoshop cc for mac free download. How to configure
Configure on Sophos XG Browser for old mac os.
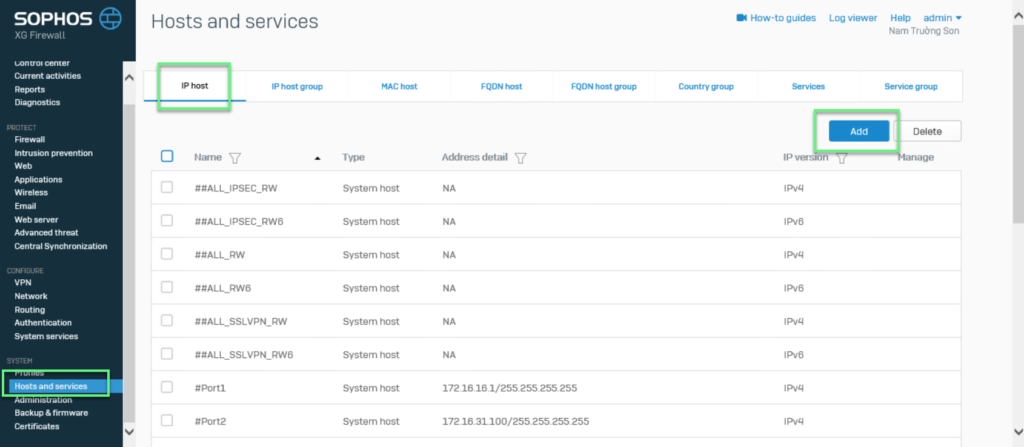
Step 1: Create Local and Remote network area for XG device
- Log in to Sophos XG by Admin account
- Hosts and Services -> IP Host -> Click Add
- Create Local Network
- Enter name
- Choose IPv4
- Choose Network
- In IP address -> Import Internal network
-> Click Save
- Create Remote Network
- Enter name
- Choose IPv4
- Choose Network
- In IP address -> Import Remote network
-> Click Save
Step 2: Create IPSec connection on Sophos XG Tony hawk 3 for mac.
- VPN -> IPSec connections -> Click Wizard
- Enter name
- Click Start
- Choose Site To Site
- Choose IKEv2
- Click >
- Choose Preshared key
- Enter Preshared key (using for both site)
- Click >
- Choose WAN port of Sophos XG
- Choose Local Network which is created before
- Click >
- Enter IP WAN of Pfsense
- Choose Remote Network which is created before
- Click >
- Choose Disabled
- Click >
- Click Finish
- Click Active

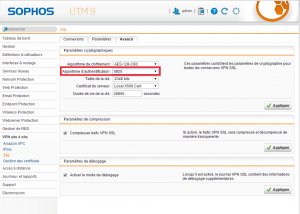
Configure on Pfsense firewall
Step 3: Create IPSec connection on Pfsense (P1)
- Log in to Pfsense firewall by Admin account
- VPN -> IPSec -> Click Add P1
- In Key Exchange version: Choose IKEv2 (same with Sophos)
- In Internet Protocol: Choose IPv4
- In Interface: Choose WAN
- In Remote Gateway: Enter IP WAN of Sophos
- In Authentication Method: Choose Mutual PSK
- In Pre-Shared Key: Enter Preshared Key which the same with Sophos
- In Encryption Algorithm: Choose AES -> 256 bits -> SHA256 -> 14 (2048 bit)
- In Lifetime (Seconds): Enter 3600
-> Click Save
Step 4: Create IPSec connection (P2)
- In Local Network: Choose Lan subnet
- In Remote Network: Enter Local network of Sophos
- In Protocol: Choose ESP
- In Encryption Algorithms: Choose AES -> 256 bits (same with Sophos)
- In Hash Algorithms: Choose SHA256
Pfsense Sophos
-> Click Save
Step 5: Create Firewall rule in Sophos to allow VPN and LAN network connect together
Pfsense Sophos Sg
Step 6: Click Connection to finish
Configure create Firewall rule for Pfsense to finish
** If you have difficulty configure Sophos products in VietNam, please contact us:
Pfsense Sophos Xg
Hotline: 02862711677
Pfsense Sophos Xg Ipsec
Email: info@thegioifirewall.com
Sophos Vs Pfsense
YOU MAY ALSO INTEREST
